Impact of Emerging Technologies
Any new technology that comes, it is bound to have some impact whether it is good or bad. Here we will see some of the emerging technologies in the field of computers and how they impact our daily lives.
What is the impact of emerging technologies?
The following are some of the new technologies which could have an impact in our everyday lives.
Robotics
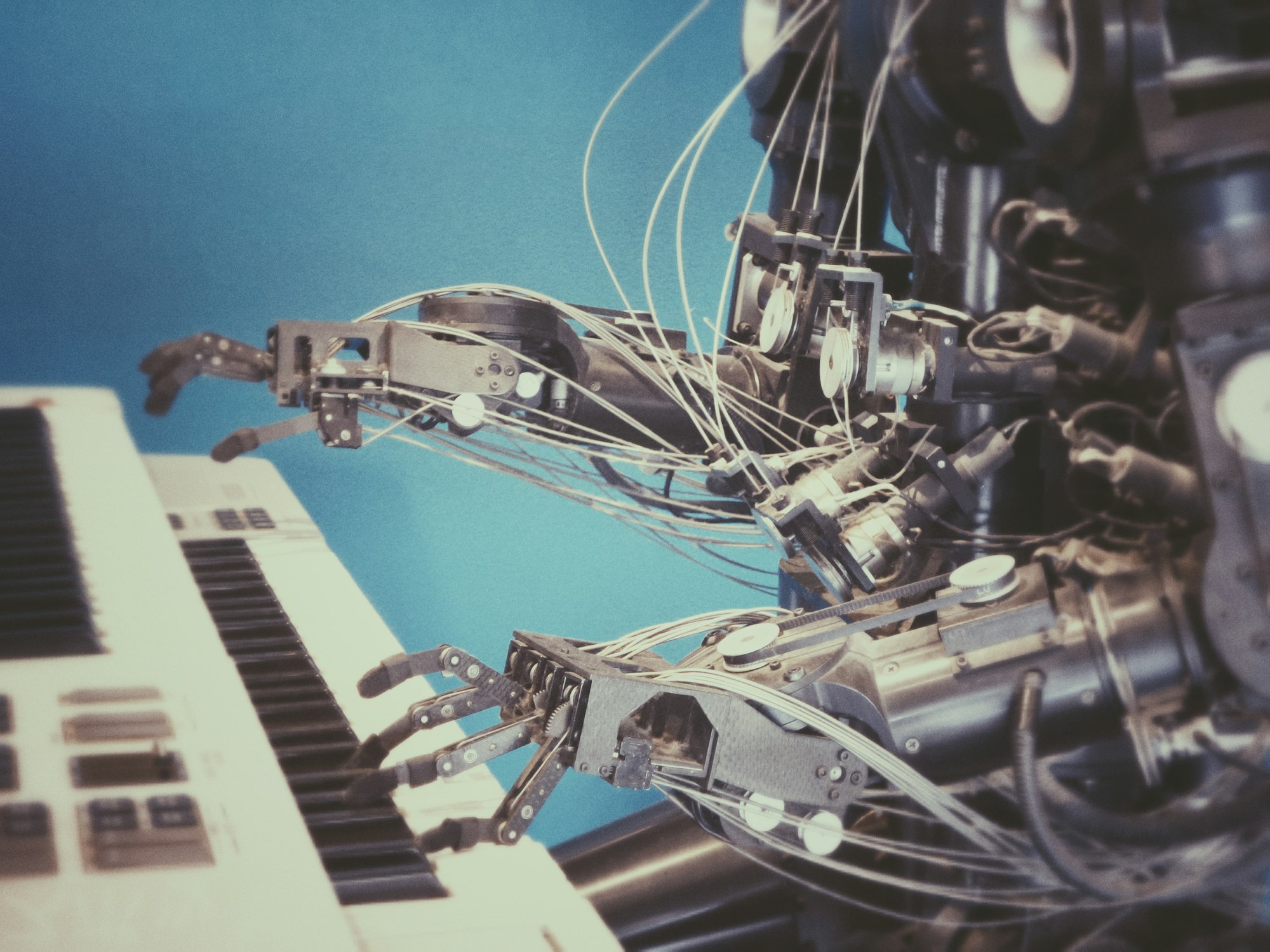
Robotics has been existence for many years now mainly in the manufacturing industry. They are used in car factories to weld car bodies, spray painting of body parts and fit items, etc resulting in near zero human intervention.
However, new areas outside manufacturing are rapidly evolving where robotics has started to make inroads.
One application is the use of Robots as waiters in many high end restaurants.
Another application is in the use of drones. These are unmanned flying devices that are used both by the armed forces and civilians. The armed forces have been using drones for reconnaissance missions for quite a number of years now. In the civilian domain, they are being used for surveying the landscape in 3-D for use with GPS, for crowd control in case of any mass gatherings, investigating weather phenomena like tornadoes and hurricanes or similar work, where it would be too dangerous for manned surveillance for search and rescue/fire fighting in natural disasters.
Another area is in the field of medicine, where robots are used in surgical procedures. Robotic surgery is allowing surgeons to perform even the most complex surgical procedures with precision, flexibility and control than standard surgical techniques. In this, surgeons use robotics equipped with a camera arm and several interactive mechanical arms, which work like a human wrist to perform a surgery.

Vision Enhancement
Here, there is Low Vision Enhancement System (LVES) and Night Vision Enhancement (NVE).
The Low Vision Enhancement system uses video technology in the headset which is connected to a computer. The system allows images to be projected inside the headset in front of the eyes. This effectively brings the object closer for examination for the wearer of the system.
The Night Vision Enhancement system amplifies infrared light and visible light so that the image can still be seen in apparent darkness. The armed forces generally use this technology to carry out surveillance at night. The dim light source from the area under surveillance is captured and passed through an image intensifier tube, which will convert the light into electrons. These electrons then pass through another tube where they are amplified to produce several times the original number of electrons. These electrons then hit a screen kept at the end of the tube. As this screen is coated with phosphor dots that glow when the electrons collide with them, it results in an image that is considerably clearer than the original.
Artificial Intelligence (AI) biometrics
A well known problem with biometric technology is that many fingerprint identification systems fail to detect a person's fingerprints when they are checked against the database in which it is stored.
Artificial Intelligence (AI) biometrics overcomes this problem by a technique called dynamic profiling where the system learns by using AI about a person's fingerprints on every scan, which means that a person does not have to worry about getting his/her finger in exactly the right place every time on the scanner. How the system works is, it learns from different alignments and is therefore still able to match the fingerprints to those stored in the database.
Facial-recognition systems also have the same problem. A human being is still able to recognise a face even if that person has grown facial hair, wears glasses now or has aged. Whereas computerised facial-recognisition systems get confused by such soft biometric changes. New systems use AI to learn from scanning a number of faces and can pick out these soft biometric features, which means the system can still recognise faces and cross-reference these attributes with the corresponding images stored in the database.
Virtual reality
Virtual reality is an artificial environment which is created by software. The user wears data goggles, sensor suits, data gloves or helmets to get a feeling of reality (that is, the feeling of being there). This technology is used in education, for example, to explore the inside of a a cave in a geology lesson, in training, for example, in a nuclear reactor, where the user can see all the walls, pipes, vessels and valves as if one is inside the reactor, so that one can be trained safely to deal with certain events or in games where the user can interact as if he/she is there, such as a driving simulator, where the road ahead is output on to a visor in a helmet strapped to the user's head.
There are various applications of Virtual reality namely:
- Military applications like training to use a new tank.
- Aviation like training to fly a new plane.
- Heritage like showing monuments such as Taj Mahal.
- Fashion like using in stores so that a customer can actually see how the clothes will look on him/her without actually wearing it.
- Entertainment like games where gloves, goggles or helmets are worn to give realism to the scenario and even to give images or sound to make it seem very real.
- Education like looking inside a cave or volcano as part of a geology lesson.
- Healthcare as a diagnostic tool.
- Business like training courses and role-playing scenarios for staff.
- Scientific visualisation like looking at molecular structures in chemistry.
- Sports like in cricket to improve a player's technique in hitting the ball with the bat or throwing the ball towards the batsman.
- Engineering like seeing how new designs will look.
- Media like special effects in films like Spider Man/Jurassic Park.
Quantum Cryptography
Cryptography is the science of making a message unintelligible to any unauthorised person (a hacker). This technique is often referred to as encryption. Many methods of cryptography are in existence today but all of them have a limited life as computers become faster and faster at number crunching. A direct victim of this is that, over the next few years, a hacker is more likely to decipher encrypted messages unless computer designers are able to further strengthen security systems.
Quantum cryptography is based on the use of photons or light and their physical quantum properties to produce a virtually unbreakable cryptographic system. This helps protect the security of the data being transmitted over fibre-optic cables. The technology relies on the fact that photons oscillate in various directions and produce a sequence of random bits (0s and 1s) across the optical network. It is based on the laws of physics rather than mathematics which is how current cryptography works.
Computer-assisted translation (CAT)
Existing online language translators have a very limited use.
Consider the case of the insect called fruit fly which is particularly fond of eating bananas. Now, if we typed in the phrase 'fruit flies like a banana', this could translated into German using a free online translator as 'fruchtfliegen wie eine banane'. This statement in German only refers to the banana-shaped flight path of a piece of fruit thrown through the air!. Imagine a scenario, where a whole page is being translated that is full of such double meanings of words and phrases.
Computer-assisted translation (CAT) goes some way to overcome these issues. CAT is a type of language translator that uses specific software to help in the translation process.
In particular, CAT uses two tools:
- terminology databases meaning linguistic databases that grow and 'learn' from translations being carried out.
- translation memories meaning these automatically insert known translations for certain words, phrases or sentences.
All CAT software needs some post-editing by the user to remove erros from the translation process. While they may not be perfect, they are certainly more accurate than existing free online translators.
3-D and holographic imaging
Holography is a technology that allows one to make 3-D images known as holograms to be produced. The technology involves the use of:
- A source of laser light
- Interference of light
- Light diffraction and
- Light intensity recording
As a holographic image is rotated, it appears to move in the same way as the original object, thus giving a feeling of three dimensions (3-D). The hologram is produced by first splitting a laser beam. Half of the light known as object beam is reflected off the object on to a photographic plate. The other half of the light known as the reference beam is reflected off a mirror and on to the same photographic plate. The holographic image is produced where the two light beams meet on the photographic plate.
Holograms have many applications, some of the well know being in:
- Architecture (ability to rotate design through 360 degrees.
- Simulations
- Cinema for special effects
- Advertising
- Gaming for special effects
- Optical computers (these computers will operate at speeds that are trillions of times faster than current technology computers
- Engineering design for example CAD
- Medical imaging to see inside organs in 3-D - links into tomography, which is the same technology behind 3-D printers.
- Holographic computer memories which is a new type of optical storage, a crystal the size of a sugar cube can hold upto 1 TB of data.
- Holographic televisions which is expected latest by 2025, which should give a full 3-D experience without the need for special glasses. Just to give a head start, the first such TV has recently been patented by a leading TV manufacturer but is yet to start commercial production.
This is the end of this guide. Hope you enjoyed it! Thanks for using www.igcsepro.org! We hope you will give us a chance to serve you again! Thank you!
